DevOps + Security = DevSecOps

Integrating security into the software development process is a good practice. DevSecOps aims to ensure that security is integrated throughout the software development lifecycle, from development to deployment. Various tools are available to help security and development teams collaborate more effectively to achieve this goal.
In this article, we will look at some DevSecOps tools and which ones to use based on your unique needs and goals. Before we get into the tools required to implement DevSecOps, which is the main goal of this article, we must first understand DevOps, DevSecOps, and the distinction between the two.
Let’s get started.
Who is this article for?
DevOps and DevSecOps are interdisciplinary practices that involve the collaboration and communication of various individuals and teams within a company. As a result, the following individuals should understand DevOps and DevSecOps:
- Developers: They are in charge of writing code and creating applications. They must understand how to set up Continuous Integration and Continuous Delivery (CI/CD) pipelines and automate testing and deployment.
- Project Managers: To effectively manage the development and release of software projects, they must understand DevOps and DevSecOps practices.
- Business Stakeholders: These are the people in charge of making software development and release decisions. They must understand the advantages of DevOps and DevSecOps, such as faster time to market, high-quality software, and enhanced security.
- Operations Teams: They are in charge of maintaining and managing production systems. They must understand how to collaborate with developers to release and deploy code quickly and efficiently.
- Security Teams: These teams are in charge of ensuring an organization’s system and data security. They must understand how to incorporate security into the development process and collaborate with developers and operations teams to ensure application security.
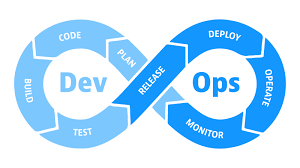
What is DevOps?
DevOps (Development and Operations) is a software development method that seeks to close the gap between development and operations. This emphasizes collaboration, communication, and integration between software developers and IT operations teams throughout the entire Software Development Life Cycle (SDLC).
DevOps is a combination of the development (Dev) and operations (Ops) processes of SDLC.
DevOps is intended to boost efficiency, speed up the delivery of new software features, and improve software application quality. Automation, continuous integration, continuous delivery, and continuous deployment are used to achieve this. DevOps aims to enable organizations to deliver high-quality software that meets the needs of their customers quickly and reliably.
What is DevSecOps?
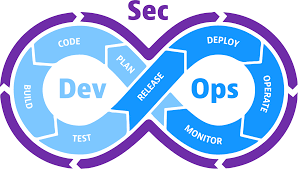
DevSecOps (Development, Security, and Operations) is a software development method that takes priority collaboration and communication among software development, security, and operations teams throughout the SDLC. DevSecOps aims to integrate security into the DevOps lifecycle. It automates security testing and integrates security tools and processes into the development pipeline, thereby adding security to the development process. This aids in identifying and addressing security vulnerabilities early in the SDLC. It also lowers the risk of security breaches and improves the software’s security posture.
DevSecOps aims to shift security left by embedding it into the development process. This ensures that security is not introduced at the end of the development process but is built into the structure of the software from the beginning.
Difference between DevOps and DevSecOps
DevOps and DevSecOps are two concepts in software development that are related but have different focuses.
DevOps is a collection of practices and processes aimed at improving collaboration and communication between software development and IT operations. DevOps’ primary goal is to automate the software delivery pipeline to make it more efficient, faster, and reliable.
DevSecOps is a DevOps extension that focuses on incorporating security into the software development life cycle. DevSecOps seeks to ensure that security is considered at all stages of development, from planning to deployment and maintenance. It aims to identify and mitigate security risks as early in the development process as possible so that security is built into the software from the start.
The image below illustrates the differences between DevOps and DevSecOps
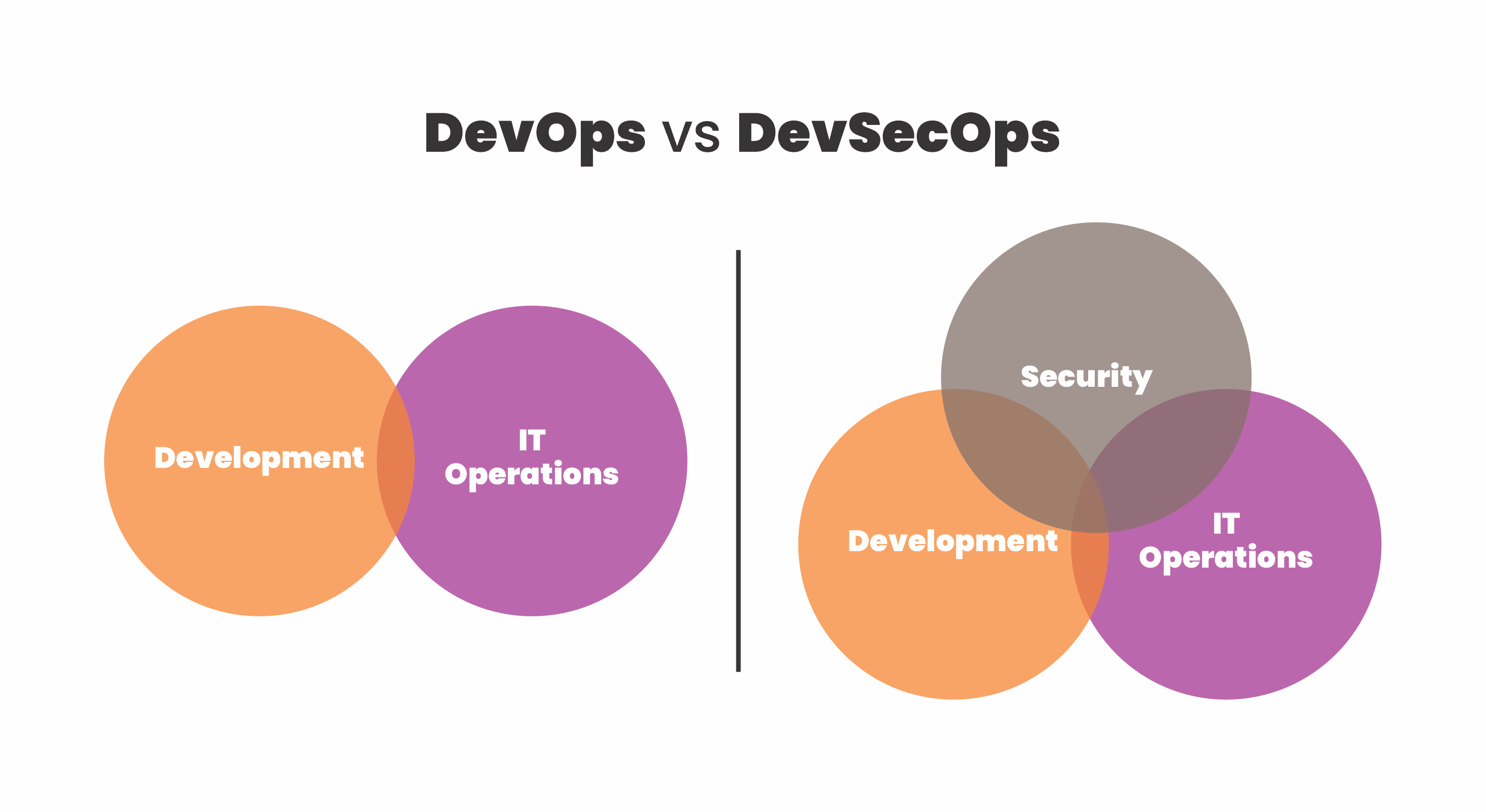
In summary, DevOps improves collaboration and communication between development and operations, whereas DevSecOps integrates security throughout the software development process.
Advantages of DevSecOps over DevOps
- Early detection of code vulnerabilities
- Increased agility and speed for security teams
- The ability to respond quickly to change and needs
DevSecOps Tools and Functions
DevSecOps Tools are generally classified into the following categories:
-
Code Analysis and Scanning Tools: These tools scan source code for vulnerabilities and security issues and provide feedback and recommendations to developers on how to fix them. Here are some examples:
- SonarQube: This is an open-source platform developed by SonarSource. It performs a static code analysis to detect security, maintainability, and reliability issues. JavaScript, TypeScript, Python, C#, C++, HTML, CSS, PHP, and many other languages.
- Veracode: This is a cloud-based application security testing service that includes static code analysis, dynamic analysis, and software composition analysis. It supports a wide range of languages, including C++, JavaScript, Java, Python, Node.js, Swift, COBOL, and others.
- Checkmarx: This is a commercial tool that performs static code analysis and vulnerability scanning for a variety of programming languages, including JavaScript, PHP, Java,.NET, C+, Swift, Go, Ruby, Python, and others.
-
Container Security Tools: Containers are a popular way to package and deploy software. They are used to deploy cloud-native applications, and numerous tools are available to provide container security. Here are some examples:
- Docker Security Scanning: A tool that scans Docker container images for vulnerabilities and reports any security issues that are encountered.
- Clair: Clair is an open-source container security scanner that detects vulnerabilities in Docker images and generates a detailed report on the containers’ security status.
- Sysdig: This is a container security platform that can provide deep visibility into the container environment, detect threats, and track security in real time.
-
Continuous Integration and Continuous Deployment (CI/CD) Tools: CI/CD tools automate the process of developing, testing, and deploying software. Some include security features or can be integrated with other security tools. Here are some examples:
- Jenkins: This is an open-source CI/CD automation server. It enables developers to create, test, and deploy applications. Jenkins supports a variety of programming languages, including Java, Ruby, Python, and others.
- CircleCI: This is a cloud-based CI/CD platform that automates software builds, tests, and deployments. Languages supported include Node.js, Python, Ruby, and others.
- GitLab: A web-based Git repository manager that allows for continuous integration, continuous delivery, and security scanning. It is compatible with DevOps workflows such as code review, issue tracking, and project management.
- Travis CI: Another cloud-based CI/CD platform. It enables developers to create and test applications in a variety of programming languages, such as Python, Node.js, Ruby, and others.
-
Infrastructure as Code (IaC) Tools: IaC tools enable organizations to manage their infrastructure as code, making automation and management easier. Some of these tools include security features like automated vulnerability scanning and remediation. Here are some examples:
- Terraform: This is an open-source tool that allows you to create, change, and version infrastructure. It works with a variety of cloud providers and can manage infrastructure resources like virtual machines, databases, and network interfaces.
- Ansible: Ansible is a free and open-source automation tool for configuration management, application deployment, and task automation. It defines infrastructure as code using YAML, a human-readable language.
- Chef: Chef is a configuration management tool that defines infrastructure as code using a Domain-Specific Language (DSL). It automates the configuration and deployment of infrastructure and applications.
-
Security Testing Tools: These tools perform a variety of security tests, including penetration testing, web application security testing, and network security testing. Here are some examples:
- OWASP ZAP: An open-source web application security scanner that detects flaws in web applications. For automated scanning, it can be integrated into the DevSecOps pipeline. This includes languages such as Java, Python,.NET, Ruby, and others.
- Nessus: A vulnerability scanner used to test applications and infrastructure for security breaches. It is used in a DevSecOps environment to automate security testing.
- Burp Suite: This is a collection of tools for testing the security of web applications. It comes with a scanner, proxy, and other tools for testing vulnerabilities. Burp Suite supports a variety of languages, including Java, Python,.NET, Ruby, and others.
-
Monitoring and Log Management Tools: These tools provide visibility into the behavior and performance of applications and infrastructure, as well as aid in the detection of potential security incidents. Here are some examples:
- Splunk: A popular monitoring and log management tool that provides real-time analytics, visualization, and insights into machine data from a variety of sources. It supports a wide range of use cases, including security, IT operations, and business intelligence, and provides flexible data collection, search, and analysis capabilities.
- Sumo Logic: This is a cloud-based log management and analytics platform. It provides real-time insights into application and infrastructure data. It supports advanced search and visualization, as well as machine learning-powered analytics and anomaly detection.
Other DevSecOps tools are available, depending on an organization’s specific needs and requirements.
Session Replay for Developers
Uncover frustrations, understand bugs and fix slowdowns like never before with OpenReplay — an open-source session replay tool for developers. Self-host it in minutes, and have complete control over your customer data. Check our GitHub repo and join the thousands of developers in our community.
DevSecOps Workflow
The stages of the DevSecOps workflow are as follows:
- Planning: Defining the scope of the project, outlining the goals, and determining the requirements are all part of this stage. The team also identifies potential security risks and decides on the security controls that must be implemented at this stage. Tools include Trello, Asana, and others.
- Development: During this stage, code is written and tested. It ensures the code’s security and functionality. Tools include Git, GitHub, GitLab, Jenkins, CircleCI, and others.
- Testing: At this stage, the code is tested to ensure that it meets the defined security requirements. The goal of this stage is to find and fix any security flaws before releasing the code. Tools include OWASP ZAP, SonarQube, Veracode, Nessus, and others.
- Deployment: At this stage, the code is deployed to the production environment. This stage’s goal is to ensure that the code is securely deployed and that the environment is configured to support the application. Available tools include Ansible, Docker, Kubernetes, and more.
- Monitoring: At this stage, the application is monitored to ensure that it continues to function securely and to identify any potential security issues. Splunk, ELK Stack, Nagios, and other tools are available.
DevSecOps workflow is intended to incorporate security into all stages of its lifecycle.
Best Practices
- Educate and train: Developers and security teams should be trained on security best practices and emerging threats on a regular basis. This ensures that they are up to date with the most recent security measures and can identify potential vulnerabilities during the development process.
- Automate Security Testing: Implement continuous automated security testing at every stage of the development process. Automated testing tools can detect security flaws such as SQL injection and cross-site scripting (XSS) and assist developers in resolving them before the application is released. Penetration testing should be performed on a regular basis to identify potential security breaches.
- Implement Security as Code: One of the core DevSecOps principles is that security must be treated as code. This means that security measures like authentication and authorization should be implemented through code and version-controlled alongside the application code. It helps to ensure that security is built into the development process and allows for automated testing and deployment of security features.
- Implement Least Privilege Access: Developers should only have access to the resources necessary to complete their tasks. It aids in minimizing the potential harm caused by human error or malicious activity. Introduce the use of Multi-factor authentication to ensure that only authorized personnel have access to sensitive data and systems.
- Use Containerization: This can help ensure the security of applications by isolating them from the host environment. Containers are self-contained and run in their own virtual environment, making applications easier to manage and secure.
- Secure the Pipeline: It is important to ensure that the pipeline used for continuous integration and continuous deployment is secure. This includes securing the pipeline’s servers, ensuring that only authorized personnel have access to the pipeline, and implementing secure communications between pipeline components.
Conclusion
So far, we’ve talked about some DevSecOps tools and their capabilities. Security is critical in the Software Development Life Cycle (SDLC) because it eliminates the burden of starting to test for security after the SDLC is completed. These tools will aid in the integration of security across all SDLC phases.

